Diferencia entre revisiones de «Anti Spam Guide»
| Línea 45: | Línea 45: | ||
According to SMTP protocol, a returned message (bounce message), also called '''Non-Delivery Report/Receipt (NDR)''' is an automatic message generated when there is a problem delivering a message. Providers such as Hotmail usually send some NDR when there are SPAM-related problems. NDRs contain a code that specifies the reason by which the mesaage has been returned.[https://mail.live.com/mail/troubleshooting.aspx Here] you can see a list with a meaning for every code ("SMTP error codes" section). This message is very helpful on correctly doing a Delist in Hotmail. | According to SMTP protocol, a returned message (bounce message), also called '''Non-Delivery Report/Receipt (NDR)''' is an automatic message generated when there is a problem delivering a message. Providers such as Hotmail usually send some NDR when there are SPAM-related problems. NDRs contain a code that specifies the reason by which the mesaage has been returned.[https://mail.live.com/mail/troubleshooting.aspx Here] you can see a list with a meaning for every code ("SMTP error codes" section). This message is very helpful on correctly doing a Delist in Hotmail. | ||
| − | ==== | + | ====How do I connect via SSH?==== |
| − | + | To connect via SSH you will need both the username and the IP address and the password. You will be able to see this information in the Gigas control panel. | |
| − | + | Below is a guide to connect via SSH with the most common desktop operating systems. | |
| − | [http://www.softzone.es/manuales-software-2/uso-basico-de-putty-ssh/ | + | [http://www.softzone.es/manuales-software-2/uso-basico-de-putty-ssh/ Guide to connect via SSH in Windows.] |
| − | [http://www.ehowenespanol.com/utilizar-ssh-mac-x-como_85688/ | + | [http://www.ehowenespanol.com/utilizar-ssh-mac-x-como_85688/ Guide to connect via SSH on Mac.] |
| − | [http://davidburgosonline.com/devops/2012/como-conectarse-por-ssh-via-terminal/ | + | [http://davidburgosonline.com/devops/2012/como-conectarse-por-ssh-via-terminal/ Guide to connect via SSH in Linux.] |
| − | + | Once we connect via SSH, we can give orders to the server. | |
| − | ==== | + | ====How do I view the mail queue?==== |
| − | + | The mail queue is a space reserved for emails that have not been delivered for any reason or that are going to be delivered. When we have SPAM problems, the mail servers reject our connection and the emails remain in the queue to be delivered again after a while. To check the messages in the mail queue, you can do it in the following way: | |
| − | * | + | *By SSH: you have to log in via SSH and run the command postqueue -p |
| − | * | + | *Plesk Panel: you have to go to Tools and settings > Mail > Mail server settings > Mail queue. By clicking on the subject of the message you will be able to see the email headers. |
| − | === | + | ===Do you send newsletters that are classified as SPAM?=== |
| − | + | If you send a lot of newsletters, it is possible that you are classified as a spammer because you have sent a lot of emails very quickly to many accounts (the same as spammers do). We recommend that before sending a newsletter you check if it is well-formed so that the anti-spam filters classify it as SPAM or not. This website may be of great help: [http://spamscorechecker.com spamscorechecker.com]. | |
| + | ==Main symptoms== | ||
| − | + | In this section we will analyze the main symptoms that make us see that we are suffering a blockage or have a low reputation. | |
| − | + | Email service providers take many measures and checks before accepting an email. These checks are what determine whether an email should go to the inbox, the SPAM folder, should be returned or should not be delivered. All this depends on our reputation. | |
| − | + | When an email goes to the SPAM folder, the main symptom is that our recipient does not see the email (or sees it in the SPAM folder). | |
| − | + | When an email is bounced when sending an email, the mail server will return it to us with an error code and the reasons why it was bounced. | |
| − | + | When an email is not delivered, the messages will be queued on your mail server to be re-delivered after a set time. We will also get an error code to know the reasons for the rejection. | |
| − | + | ===Reasons and solutions=== | |
| − | + | To explain it in a simpler way, let's say that our IP and domain have a reputation on the Internet that is estimated based on several parameters. One of them is the blacklists, which evaluate whether an IP (or range) has been sending spam. Other providers such as Hotmail or Gmail have their own methods (in the case of Hotmail it is called smartscreen) and there are times when their verdict will have nothing to do with the blacklists (both for good and for bad). Another very important thing is to have a correct configuration so that when the time comes when they ask us about our “identity”, we are clear and honest enough so that they do not doubt us. This will lead to better data verification and therefore a better reputation. | |
| − | + | ==Basic configuration== | |
| − | == | + | ===How can I check that I have configured it correctly?=== |
| − | + | You can use the website [http://www.mail-tester.com mail-tester.com] to check your score regarding the configuration. It involves sending an email to the address they tell you and once you do it you will be able to see if your configuration is correct or not, indicating the errors if you have them. More directly you can check [https://www.mail-tester.com/spf-dkim-check here] your SPF (you have to put the domain) and the DKIM (the selector is usually "default"). | |
| − | + | ===I haven't had a good score :(=== | |
| − | + | If you haven't had a good score in the checker from the previous point, you have to configure the basic elements so that they don't doubt our identity. | |
| − | + | ||
| − | + | ||
====HELO / PTR==== | ====HELO / PTR==== | ||
| − | + | The HELO is one of the steps of the SMTP protocol. It is like asking a mail server what is your name? This parameter is configured on the mail server, but on servers with panels the change has to be done through the panel. Below we detail how to change the HELO both in Linux without a panel and in Linux with a panel: | |
<ul> | <ul> | ||
| − | <li>Linux | + | <li>Linux without panel: |
<ol type="a"> | <ol type="a"> | ||
| − | <li> | + | <li>Change the parameters myhostname and smtpd_banner in the /etc/postfix/main.cf file (they must contain a subdomain that resolves via DNS).</li> |
| − | <li> | + | <li>The command postconf -e myhostname=mail.yourdomain.com also works</li> |
</ol> | </ol> | ||
</li> | </li> | ||
</ul> | </ul> | ||
| − | *Linux | + | *Linux with cPanel: put in "Network Settings > Change Server Name > New Server Name" a domain that is on the VPS and that resolves. |
| − | *Linux | + | *Linux with Plesk: put in "Start > Tools and Settings > Tools and Settings > Server Settings > System Settings > Full Host Name" a domain that is on the VPS and that resolves. |
====SPF==== | ====SPF==== | ||
| − | + | The [https://es.wikipedia.org/wiki/Sender_Policy_Framework SPF] is a TXT type DNS record that indicates who can send emails on behalf of that domain. Anti-spam filters, when doubting the reputation of an IP or the authenticity of an email, ask themselves "Can the IP that sent me this email send on behalf of that domain?" and, then, it is the SPF that answers the question "Who can send emails on behalf of my domain?". | |
| − | ===== | + | =====Do I have my SPF configured? How do I know what my SPF is?===== |
| − | + | To check your SPF you can use many online checkers like [http://www.kitterman.com/spf/validate.html this one]. | |
| − | + | An example of SPF could be the following: | |
<pre>v=spf1 ip4:146.255.99.195 include:_spf.google.com -all</pre> | <pre>v=spf1 ip4:146.255.99.195 include:_spf.google.com -all</pre> | ||
| − | + | If there is no SPF in the checker we will get the following text: | |
<pre>No valid SPF record found of either type TXT or type SPF.</pre> | <pre>No valid SPF record found of either type TXT or type SPF.</pre> | ||
| + | =====Where do I configure my SPF?===== | ||
| − | + | As we have already defined, the SPF is a TXT type DNS record. That is, you will have to add it in your DNS configuration panel. If you do not have the domain contracted with Gigas, the panel is that of your domain provider. In the case where you have changed the NS records and have put them in the type yourip.dnsgigas.es ([[How_to_use_the_DNS_of_my_Gigas_server_if_my_domain_is_registered_with_another_provider|here is a tutorial]]), the panel will be cPanel or Plesk. Therefore the SPF records will be automatically configured by the panel. In the case that you do not have a panel, the TXT record configuration must be done manually on the DNS server. | |
| − | + | If you do not remember where you configure your DNS records, go to https://www.whatsmydns.net/#NS and check your domain (you must put your domain in the white box and the record type: NS). | |
| + | *If after clicking on search, the answer is dns0[1,2,3 and 4].gigas.com, you must do the configuration from your Gigas panel. *If the answer is of the type tuip.dnsgigas.es and tuip.ns2.dnsgigas.es, you have to configure it through the panel you have (Plesk or cPanel). | ||
| + | *If the result is another, copy and paste the answer and make a query of type A, it will tell you the IP in which you have to configure it. | ||
| − | + | =====What do I put as SPF?===== | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | The SPF has a defined structure, that is, you cannot put something without sense. To generate your SPF record, it is best to enter [http://www.spfwizard.net/es/ this wizard] and answer the questions it asks you. Once you finish, you will have to put the record that it generates at the top. In the case that you put it through a panel, the type would be TXT and the content would be what is between quotes. | |
| − | + | ||
| − | + | ||
====Domain Keys / DKIM==== | ====Domain Keys / DKIM==== | ||
| − | [https://es.wikipedia.org/wiki/DomainKeys DomainKeys] | + | [https://es.wikipedia.org/wiki/DomainKeys DomainKeys] is an authentication mechanism to verify that the person who sent the email is really who they say they are. In short, when antispam filters wonder about the veracity of the email they just received, they ask themselves: is this user really who they say they are? and DomainKeys gives that answer. |
| − | + | Below we detail how to enable DomainKeys both on Linux without a panel and on Linux with a panel: | |
| − | *Linux | + | *Linux without a panel: you will have to search Google for how to do it for your mail server (usually postfix) and your Linux distribution since there is no unique way to do it. |
| − | *Linux | + | *Linux with Plesk: |
| − | *# | + | *#Enable the option "Start > Tools and settings > Server-level mail settings > DomainKeys antispam protection > Allow outgoing mail signing". |
| − | *# | + | *#Enable the option "Home > Subscriptions > yourdomain > Websites and domains > Mail settings > Use DomainKeys antispam protection system for signing outgoing emails". |
| − | *Linux | + | *Linux with cPanel: |
| − | *# | + | *#In cPanel go to "Mail > Email authentication" and enable "DKIM". |
| − | ==== | + | ====Sending limits==== |
| − | + | Sometimes it is good to limit the number of messages that can be sent to avoid a loss of reputation. When our server is compromised, SPAMMERS will start sending hundreds of thousands of emails around the world. By enabling these limits we will detect the problem and prevent the disaster from becoming greater. | |
| − | + | Below we detail how to limit the number of outgoing messages both in Linux without a panel and in Linux with a panel: | |
| − | *Linux | + | *Linux without a panel: since it is usually installed by advanced users, we recommend the use of [http://wiki.policyd.org/start policyd]. |
| − | *Linux | + | *Linux with Plesk: |
| − | *# | + | *#Enable the option in "Start > Tools and Settings > Server-level mail settings > Enable outgoing email restrictions". |
| − | *# | + | *#Fill in the fields as you estimate based on the use of your mail server. |
| + | ==Where can viruses be found?== | ||
| − | + | SPAM sending viruses can be found both on clients and on the server. That is, they can be on your own computer or mobile device, as well as on your own server. | |
| − | + | ===Viruses on clients=== | |
| − | + | There are times when devices are infected with the sole purpose of sending SPAM through mail programs. You should check all the devices that have had access to your server's mail accounts with several antivirus programs. | |
| − | + | In the case where the emails stay in the mail queue, in the '''headers of queued emails''' there may be important information in the '''X-Mailer''' section. This is where it usually appears from where the email was sent (for example Windows Live Mail, iPhone, etc.). | |
| − | + | Other times, what happens is that one of the accounts has a password very weak and it has been guessed. In that case, you will have to change the password of all users and set a stronger password (you can check the strength of your password at [http://howsecureismypassword.net/ this link]). | |
| − | + | ===Virus on the server=== | |
| − | + | Just like on the clients, you can also run an antivirus on the server. We recommend the antivirus [http://www.clamav.net/index.html ClamAV]. To run the antivirus you have to connect via SSH to your server (if you don't know how to do it, it is explained above) and install and run the antivirus (each distribution has a method). Search on the internet how to install ClamAV for your distribution. | |
| − | + | Another way to find viruses (scripts) that send mass emails is to '''enable the log of sent emails'''. | |
| − | + | In case you have a Plesk panel: | |
| + | *follow [http://kb.odin.com/en/114845 these instructions if your mail server is Postfix] (the most common) | ||
| + | *follow [http://kb.odin.com/en/1711 these instructions if your mail server is Qmail]. | ||
| − | + | ====Virus on the server. Special case of Wordpress==== | |
| − | + | ||
| − | + | ||
| − | + | The number of Wordpress that have been compromised by spammers to achieve their goal is especially large: to intervene in the server and send SPAM from other servers. It is VERY IMPORTANT that you keep both your wordpress and your plugins updated. To do this automatically, you can use [https://wordpress.org/plugins/automatic-plugin-updates/ this plugin]. | |
| − | + | It is also important that you do not use pirated paid themes since they frequently include malware to infect the servers and take control of them. There are numerous [https://wordpress.org/themes/ free themes on the Wordpress website]. | |
| − | + | ==Blacklists== | |
| − | + | There are blacklist services on the internet that detect and list IPs that are sending SPAM. Some of these blacklists are highly regarded when accepting mail from an IP and other blacklists are less so. If your server is correctly configured (please check the points above to make sure) and you are on a blacklist, it is very likely that a malicious program (hereinafter a virus) is sending mail from your server. There are many websites to check if your IP is on a blacklist such as [http://multirbl.valli.org/ multirbl] or [http://mxtoolbox.com/blacklists.aspx mxtoolbox]. | |
| − | + | It is important to note that there are "pirate" blacklists that, despite not being relevant in the fight against SPAM, ask for money to be removed from the list. Never pay for such services and do not confuse them with professional blacklist monitoring services. | |
| − | + | It is also important to note that there are certain blacklists that have checks that do not apply to everyone (for example dnsblchile.org). Therefore, they do not provide relevant information. | |
| − | + | ||
| − | + | ||
===Delist=== | ===Delist=== | ||
| − | + | Delisting is the removal of your IP from the services that are causing you problems. The major email service providers offer contact forms so that you can request that your IP not be categorized as SPAM. It is VERY IMPORTANT that you request delisting as long as you have made sure that: | |
| − | # | + | #You have the identification configuration done correctly (see section [[#Basic_configuration|Basic configuration]]). |
| − | # | + | #Your server is not compromised and therefore you are not sending SPAM unintentionally. #It is a very good idea to create contact emails such as postmaster@yourdomain.com, abuse@yourdomain.com and webmaster@yourdomain.com in the delisting process, as they give greater legitimacy to the IP and domain. |
| − | # | + | |
| − | + | If you request delisting and do not meet these three characteristics, the delisting will not be carried out and will even be harmful, as it will make it more difficult to get off the blacklist again. | |
| − | ==== | + | ====Hotmail Delist==== |
| − | + | Click here to request the [https://support.microsoft.com/en-us/getsupport?oaspworkflow=start_1.0.0.0&wfname=capsub&productkey=edfsmsbl3&locale=es-es delist in Hotmail]. During the process they will need the error message (see above [[#What_is_an_NDR?|What is an NDR?]]) that Hotmail returns when rejecting an email (you have to put it in the section that says "Copy and paste error messages:" ). It is more effective if you fill it out twice, once indicating that the domain to which it is sent is hotmail.com and another indicating that it is outlook.com. | |
| − | ==== | + | ====Gmail Delist==== |
| − | + | Click here to request the [https://support.google.com/mail/contact/msgdelivery delist in Gmail]. | |
| − | ==== | + | ====Yahoo Delist==== |
| − | + | Click here to request the [http://help.yahoo.com/l/us/yahoo/mail/postmaster/bulkv2.html delist on Yahoo]. Before requesting this delist it is important to check if you appear [http://www.spamhaus.org/lookup/ here]. | |
| − | ==== | + | ====Mail forwarding==== |
| − | ''' | + | '''It is NOT''' advisable to have an email address that forwards mail to another email provider (Gmail... Hotmail...). It may happen that we receive a large amount of emails that will be automatically forwarded to the email provider, which will cause the provider to detect that you are sending a large amount of emails (they have their own limits of emails per minute/hour) and may ban your server. Keep in mind that these providers offer paid solutions for companies and the effect achieved with forwarding is the same but for free. |
| − | == | + | ==I received an email because I'm blocked by Hotmail. What do I do?== |
| − | + | The most important thing is to make sure that the basic configuration (see section "[[#Basic_configuration|Basic configuration]]") is done correctly and to check that your server is not sending SPAM by enabling the mail log for a few hours (see section "[[#Where_can_viruses_be?|Where can viruses be?]]") | |
| − | + | If you have already checked that the configuration is correct and that you are not sending SPAM, you must register for 2 Hotmail programs to fight SPAM: [https://postmaster.live.com/snds/ SNDS and JMRP]. | |
| − | + | Once all this is done, the Hotmail delist (see section "[[#Delist|Delist]]") will most likely be successful and you will be able to send emails to Hotmail without any problem. | |
===SNDS=== | ===SNDS=== | ||
| − | [https://postmaster.live.com/snds SNDS] (Smart Network Data Service) | + | [https://postmaster.live.com/snds SNDS] (Smart Network Data Service) is a web program that Microsoft makes available to know when they have detected SPAM from your server. To find out, you have to go to [https://postmaster.live.com/snds/ this website] and validate yourself to know the data about your IP. To do this, the first thing you need is a Hotmail account. Once you log in, you will have to go to Request Access and put your IP in the "Network to request access for:" field. Once you click submit, it will ask you for an account to validate. One of several accounts should appear, such as [[mailto:abuse@yourdomain.com abuse@yourdomain.com]] which, if it does not exist, you will have to create and continue to be validated. If an account related to your domain does not appear, you will have to review the configuration guide section (the PTR is not being detected). |
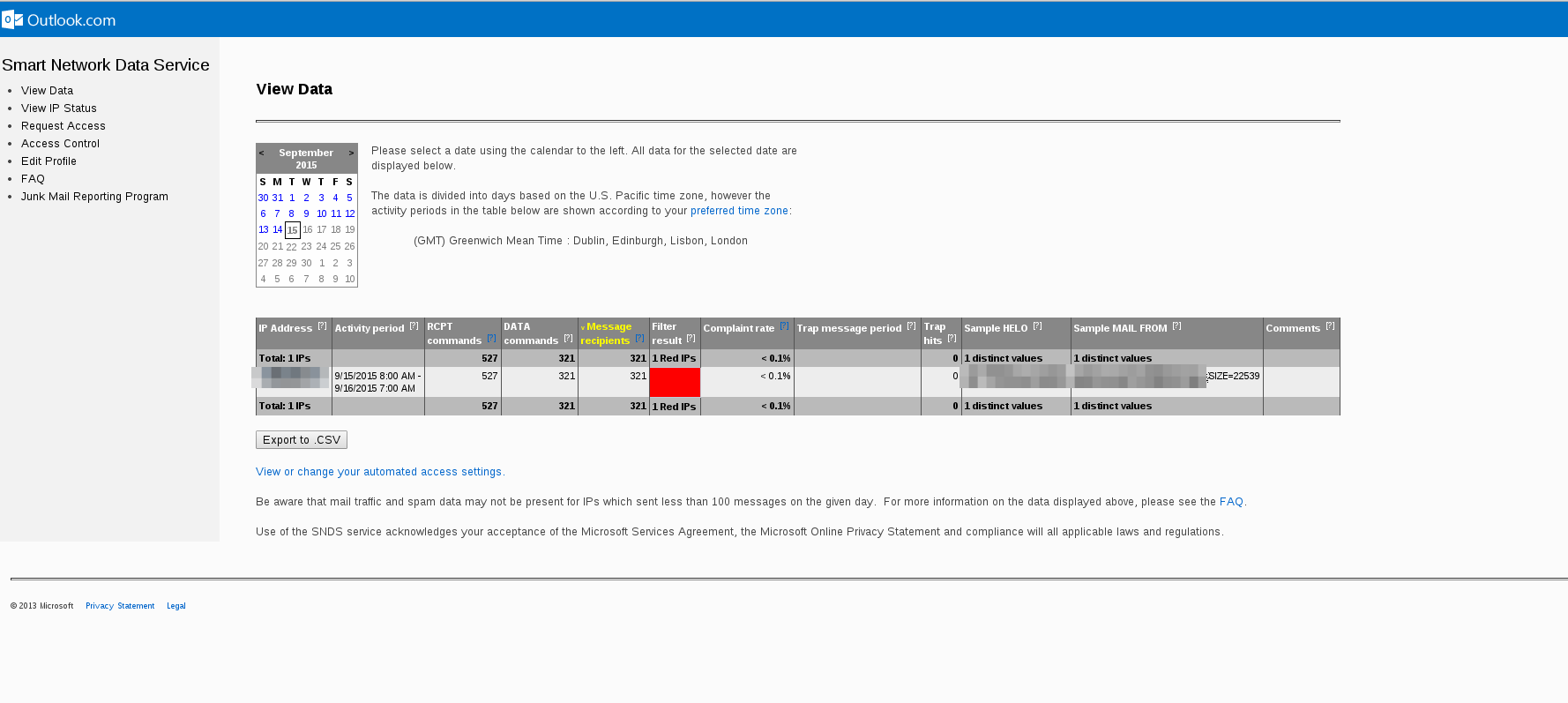
| − | ''' | + | '''Important''': the request must be made to an account that you have access to. We, at Gigas, cannot accept any request made to @gigas.com accounts. Don't worry about the rest of the accounts, they are part of an automated validation process carried out by the SNDS. You will receive an email to that account and once you click on the link it contains, you will be able to see the data. How? By accessing the View Data section in the SNDS portal and searching the calendar for the moment in which they detected the SPAM ( '''under this paragraph you have an example''' ). All the technical details and other information are explained in their [https://postmaster.live.com/snds/FAQ.aspx FAQ] section (only available in English). |
| − | [[ | + | [[File:GuiaContraSPam1.png]] |
===JMRP=== | ===JMRP=== | ||
| − | [https://postmaster.live.com/snds/JMRP.aspx JMRP] (Junk Mail Reporting Program) | + | [https://postmaster.live.com/snds/JMRP.aspx JMRP] (Junk Mail Reporting Program) is a web program that Microsoft makes available to find out what has been detected as SPAM from your server. Go to [https://postmaster.live.com/snds/JMRP.aspx here] (it is a section within the SNDS portal), fill in the fields with REAL data (ask in the complain format to send you the original message) and continue with the procedure (you will receive an email which you will have to digitally sign). Keep in mind that these types of commitments are highly taken into account by Microsoft both for good and for bad, that is, filling out the JMRP with the correct configuration and being sure that we are not sending SPAM maliciously can have very good consequences (the delisting will be faster and more effective). Filling out the JMRP when the configuration is incorrect or when SPAM is being sent unintentionally can have bad consequences. |
| + | |||
{{Support}} | {{Support}} | ||
Revisión actual del 11:15 13 feb 2025
This page is still being translated
Contenido
I have SPAM, what should I do?
You have to follow these three steps:
- Check that your mail configuration if ok (Basic configuration section)
- Check that you are not sending SPAM (Where are the viruses? section)
- If you have a correct configuration and you are not sending SPAM, you may ask for delist (Delist section). In the case of a Hotmail blocking, you must also read the section "I have received a mail telling me that I am blocked by Hotmail. What can I do?".
What is SPAM? A bit of history and some data
Fight against SPAM is an ongoing battle that held from many years ago, almost since the creation of the Internet. According to a Kaspersky analysis 59,2% of email is SPAM, although this level has reached a 90% value some times. Imagine thatr 9 out of 10 letters arriving your mailbox were commercial related or tried to scam you (phishing). Another point, according to this Hotmail Junkmail guide:
"We've implemented a number of mechanisms to reduce the burden of junk email which currently prevents nearly 4.5 billion email messages from reaching Outlook.com users every day!".
It is, thus, a big problem both for users and for IT professionals due to the problems of communication and scams and the great amount of resources being used to mitigate this problem.
This means two things:
- You are not the sole person affected. At Gigas we find everyday this kind of problem.
- Is a difficult-to-fix problem. By the moment, the only solution is to involve every technical and human resource so you are not identified as a SPAMMER and so the reputation of your IP improves.
Requirements to this guide
Initial concepts
Before going any further, it is mandatory to know the basic concepts for both sending/receiving mail and calculating your ip reputation.
What is an IP?
An IP address is the public address your server has to be reached from the Internet. As houses have an address based on the postal code system (street, number floor and door number), to reach your server from the Internet an IP address is needed.It is usually formed of 4 groups of numbers in the 0-255 range. For example, the real Gigas IP address is 146.255.99.196. Later on you will know how to get the address for any server.
What is SMTP?
SMTP is the protocol for mail exchange in the Internet. It contains the steps and rules that two computers have to follow in order to successfully send electronic mail between them.
What is SSH?
SSH is a protocol that lets you connect remotely to your Gigas server. By using this service you can get into a terminal in your server, from which you can run as many commands as you want. Web panels are sometimes insufficient to accomplish some tasks, so this is why connecting to some systems through SSH is sometimes necessary in order to obtains some information or carry out some change.
What is NDR?
According to SMTP protocol, a returned message (bounce message), also called Non-Delivery Report/Receipt (NDR) is an automatic message generated when there is a problem delivering a message. Providers such as Hotmail usually send some NDR when there are SPAM-related problems. NDRs contain a code that specifies the reason by which the mesaage has been returned.Here you can see a list with a meaning for every code ("SMTP error codes" section). This message is very helpful on correctly doing a Delist in Hotmail.
How do I connect via SSH?
To connect via SSH you will need both the username and the IP address and the password. You will be able to see this information in the Gigas control panel.
Below is a guide to connect via SSH with the most common desktop operating systems.
Guide to connect via SSH in Windows.
Guide to connect via SSH on Mac.
Guide to connect via SSH in Linux.
Once we connect via SSH, we can give orders to the server.
How do I view the mail queue?
The mail queue is a space reserved for emails that have not been delivered for any reason or that are going to be delivered. When we have SPAM problems, the mail servers reject our connection and the emails remain in the queue to be delivered again after a while. To check the messages in the mail queue, you can do it in the following way:
- By SSH: you have to log in via SSH and run the command postqueue -p
- Plesk Panel: you have to go to Tools and settings > Mail > Mail server settings > Mail queue. By clicking on the subject of the message you will be able to see the email headers.
Do you send newsletters that are classified as SPAM?
If you send a lot of newsletters, it is possible that you are classified as a spammer because you have sent a lot of emails very quickly to many accounts (the same as spammers do). We recommend that before sending a newsletter you check if it is well-formed so that the anti-spam filters classify it as SPAM or not. This website may be of great help: spamscorechecker.com.
Main symptoms
In this section we will analyze the main symptoms that make us see that we are suffering a blockage or have a low reputation.
Email service providers take many measures and checks before accepting an email. These checks are what determine whether an email should go to the inbox, the SPAM folder, should be returned or should not be delivered. All this depends on our reputation.
When an email goes to the SPAM folder, the main symptom is that our recipient does not see the email (or sees it in the SPAM folder).
When an email is bounced when sending an email, the mail server will return it to us with an error code and the reasons why it was bounced.
When an email is not delivered, the messages will be queued on your mail server to be re-delivered after a set time. We will also get an error code to know the reasons for the rejection.
Reasons and solutions
To explain it in a simpler way, let's say that our IP and domain have a reputation on the Internet that is estimated based on several parameters. One of them is the blacklists, which evaluate whether an IP (or range) has been sending spam. Other providers such as Hotmail or Gmail have their own methods (in the case of Hotmail it is called smartscreen) and there are times when their verdict will have nothing to do with the blacklists (both for good and for bad). Another very important thing is to have a correct configuration so that when the time comes when they ask us about our “identity”, we are clear and honest enough so that they do not doubt us. This will lead to better data verification and therefore a better reputation.
Basic configuration
How can I check that I have configured it correctly?
You can use the website mail-tester.com to check your score regarding the configuration. It involves sending an email to the address they tell you and once you do it you will be able to see if your configuration is correct or not, indicating the errors if you have them. More directly you can check here your SPF (you have to put the domain) and the DKIM (the selector is usually "default").
I haven't had a good score :(
If you haven't had a good score in the checker from the previous point, you have to configure the basic elements so that they don't doubt our identity.
HELO / PTR
The HELO is one of the steps of the SMTP protocol. It is like asking a mail server what is your name? This parameter is configured on the mail server, but on servers with panels the change has to be done through the panel. Below we detail how to change the HELO both in Linux without a panel and in Linux with a panel:
- Linux without panel:
- Change the parameters myhostname and smtpd_banner in the /etc/postfix/main.cf file (they must contain a subdomain that resolves via DNS).
- The command postconf -e myhostname=mail.yourdomain.com also works
- Linux with cPanel: put in "Network Settings > Change Server Name > New Server Name" a domain that is on the VPS and that resolves.
- Linux with Plesk: put in "Start > Tools and Settings > Tools and Settings > Server Settings > System Settings > Full Host Name" a domain that is on the VPS and that resolves.
SPF
The SPF is a TXT type DNS record that indicates who can send emails on behalf of that domain. Anti-spam filters, when doubting the reputation of an IP or the authenticity of an email, ask themselves "Can the IP that sent me this email send on behalf of that domain?" and, then, it is the SPF that answers the question "Who can send emails on behalf of my domain?".
Do I have my SPF configured? How do I know what my SPF is?
To check your SPF you can use many online checkers like this one.
An example of SPF could be the following:
v=spf1 ip4:146.255.99.195 include:_spf.google.com -all
If there is no SPF in the checker we will get the following text:
No valid SPF record found of either type TXT or type SPF.
Where do I configure my SPF?
As we have already defined, the SPF is a TXT type DNS record. That is, you will have to add it in your DNS configuration panel. If you do not have the domain contracted with Gigas, the panel is that of your domain provider. In the case where you have changed the NS records and have put them in the type yourip.dnsgigas.es (here is a tutorial), the panel will be cPanel or Plesk. Therefore the SPF records will be automatically configured by the panel. In the case that you do not have a panel, the TXT record configuration must be done manually on the DNS server.
If you do not remember where you configure your DNS records, go to https://www.whatsmydns.net/#NS and check your domain (you must put your domain in the white box and the record type: NS).
- If after clicking on search, the answer is dns0[1,2,3 and 4].gigas.com, you must do the configuration from your Gigas panel. *If the answer is of the type tuip.dnsgigas.es and tuip.ns2.dnsgigas.es, you have to configure it through the panel you have (Plesk or cPanel).
- If the result is another, copy and paste the answer and make a query of type A, it will tell you the IP in which you have to configure it.
What do I put as SPF?
The SPF has a defined structure, that is, you cannot put something without sense. To generate your SPF record, it is best to enter this wizard and answer the questions it asks you. Once you finish, you will have to put the record that it generates at the top. In the case that you put it through a panel, the type would be TXT and the content would be what is between quotes.
Domain Keys / DKIM
DomainKeys is an authentication mechanism to verify that the person who sent the email is really who they say they are. In short, when antispam filters wonder about the veracity of the email they just received, they ask themselves: is this user really who they say they are? and DomainKeys gives that answer.
Below we detail how to enable DomainKeys both on Linux without a panel and on Linux with a panel:
- Linux without a panel: you will have to search Google for how to do it for your mail server (usually postfix) and your Linux distribution since there is no unique way to do it.
- Linux with Plesk:
- Enable the option "Start > Tools and settings > Server-level mail settings > DomainKeys antispam protection > Allow outgoing mail signing".
- Enable the option "Home > Subscriptions > yourdomain > Websites and domains > Mail settings > Use DomainKeys antispam protection system for signing outgoing emails".
- Linux with cPanel:
- In cPanel go to "Mail > Email authentication" and enable "DKIM".
Sending limits
Sometimes it is good to limit the number of messages that can be sent to avoid a loss of reputation. When our server is compromised, SPAMMERS will start sending hundreds of thousands of emails around the world. By enabling these limits we will detect the problem and prevent the disaster from becoming greater.
Below we detail how to limit the number of outgoing messages both in Linux without a panel and in Linux with a panel:
- Linux without a panel: since it is usually installed by advanced users, we recommend the use of policyd.
- Linux with Plesk:
- Enable the option in "Start > Tools and Settings > Server-level mail settings > Enable outgoing email restrictions".
- Fill in the fields as you estimate based on the use of your mail server.
Where can viruses be found?
SPAM sending viruses can be found both on clients and on the server. That is, they can be on your own computer or mobile device, as well as on your own server.
Viruses on clients
There are times when devices are infected with the sole purpose of sending SPAM through mail programs. You should check all the devices that have had access to your server's mail accounts with several antivirus programs.
In the case where the emails stay in the mail queue, in the headers of queued emails there may be important information in the X-Mailer section. This is where it usually appears from where the email was sent (for example Windows Live Mail, iPhone, etc.).
Other times, what happens is that one of the accounts has a password very weak and it has been guessed. In that case, you will have to change the password of all users and set a stronger password (you can check the strength of your password at this link).
Virus on the server
Just like on the clients, you can also run an antivirus on the server. We recommend the antivirus ClamAV. To run the antivirus you have to connect via SSH to your server (if you don't know how to do it, it is explained above) and install and run the antivirus (each distribution has a method). Search on the internet how to install ClamAV for your distribution.
Another way to find viruses (scripts) that send mass emails is to enable the log of sent emails.
In case you have a Plesk panel:
- follow these instructions if your mail server is Postfix (the most common)
- follow these instructions if your mail server is Qmail.
Virus on the server. Special case of Wordpress
The number of Wordpress that have been compromised by spammers to achieve their goal is especially large: to intervene in the server and send SPAM from other servers. It is VERY IMPORTANT that you keep both your wordpress and your plugins updated. To do this automatically, you can use this plugin.
It is also important that you do not use pirated paid themes since they frequently include malware to infect the servers and take control of them. There are numerous free themes on the Wordpress website.
Blacklists
There are blacklist services on the internet that detect and list IPs that are sending SPAM. Some of these blacklists are highly regarded when accepting mail from an IP and other blacklists are less so. If your server is correctly configured (please check the points above to make sure) and you are on a blacklist, it is very likely that a malicious program (hereinafter a virus) is sending mail from your server. There are many websites to check if your IP is on a blacklist such as multirbl or mxtoolbox.
It is important to note that there are "pirate" blacklists that, despite not being relevant in the fight against SPAM, ask for money to be removed from the list. Never pay for such services and do not confuse them with professional blacklist monitoring services.
It is also important to note that there are certain blacklists that have checks that do not apply to everyone (for example dnsblchile.org). Therefore, they do not provide relevant information.
Delist
Delisting is the removal of your IP from the services that are causing you problems. The major email service providers offer contact forms so that you can request that your IP not be categorized as SPAM. It is VERY IMPORTANT that you request delisting as long as you have made sure that:
- You have the identification configuration done correctly (see section Basic configuration).
- Your server is not compromised and therefore you are not sending SPAM unintentionally. #It is a very good idea to create contact emails such as postmaster@yourdomain.com, abuse@yourdomain.com and webmaster@yourdomain.com in the delisting process, as they give greater legitimacy to the IP and domain.
If you request delisting and do not meet these three characteristics, the delisting will not be carried out and will even be harmful, as it will make it more difficult to get off the blacklist again.
Hotmail Delist
Click here to request the delist in Hotmail. During the process they will need the error message (see above What is an NDR?) that Hotmail returns when rejecting an email (you have to put it in the section that says "Copy and paste error messages:" ). It is more effective if you fill it out twice, once indicating that the domain to which it is sent is hotmail.com and another indicating that it is outlook.com.
Gmail Delist
Click here to request the delist in Gmail.
Yahoo Delist
Click here to request the delist on Yahoo. Before requesting this delist it is important to check if you appear here.
Mail forwarding
It is NOT advisable to have an email address that forwards mail to another email provider (Gmail... Hotmail...). It may happen that we receive a large amount of emails that will be automatically forwarded to the email provider, which will cause the provider to detect that you are sending a large amount of emails (they have their own limits of emails per minute/hour) and may ban your server. Keep in mind that these providers offer paid solutions for companies and the effect achieved with forwarding is the same but for free.
I received an email because I'm blocked by Hotmail. What do I do?
The most important thing is to make sure that the basic configuration (see section "Basic configuration") is done correctly and to check that your server is not sending SPAM by enabling the mail log for a few hours (see section "Where can viruses be?")
If you have already checked that the configuration is correct and that you are not sending SPAM, you must register for 2 Hotmail programs to fight SPAM: SNDS and JMRP.
Once all this is done, the Hotmail delist (see section "Delist") will most likely be successful and you will be able to send emails to Hotmail without any problem.
SNDS
SNDS (Smart Network Data Service) is a web program that Microsoft makes available to know when they have detected SPAM from your server. To find out, you have to go to this website and validate yourself to know the data about your IP. To do this, the first thing you need is a Hotmail account. Once you log in, you will have to go to Request Access and put your IP in the "Network to request access for:" field. Once you click submit, it will ask you for an account to validate. One of several accounts should appear, such as [abuse@yourdomain.com] which, if it does not exist, you will have to create and continue to be validated. If an account related to your domain does not appear, you will have to review the configuration guide section (the PTR is not being detected).
Important: the request must be made to an account that you have access to. We, at Gigas, cannot accept any request made to @gigas.com accounts. Don't worry about the rest of the accounts, they are part of an automated validation process carried out by the SNDS. You will receive an email to that account and once you click on the link it contains, you will be able to see the data. How? By accessing the View Data section in the SNDS portal and searching the calendar for the moment in which they detected the SPAM ( under this paragraph you have an example ). All the technical details and other information are explained in their FAQ section (only available in English).
JMRP
JMRP (Junk Mail Reporting Program) is a web program that Microsoft makes available to find out what has been detected as SPAM from your server. Go to here (it is a section within the SNDS portal), fill in the fields with REAL data (ask in the complain format to send you the original message) and continue with the procedure (you will receive an email which you will have to digitally sign). Keep in mind that these types of commitments are highly taken into account by Microsoft both for good and for bad, that is, filling out the JMRP with the correct configuration and being sure that we are not sending SPAM maliciously can have very good consequences (the delisting will be faster and more effective). Filling out the JMRP when the configuration is incorrect or when SPAM is being sent unintentionally can have bad consequences.